Securely access generated PDFs
We provide a presigned AWS S3 URL for the generated PDFs by default. However, we also offer other methods for secure access to the generated PDF.
Below are three options to safeguard the generated PDFs.
Option 1: Use an AWS pre-signed URL
A pre-signed URL is a URL that you can provide to your users to grant temporary access to the generated PDFs.
In the create PDF API, if export_type to "json", we return a JSON response back to you, and the PDF is stored on our CDN (AWS S3). In the JSON response, there is an AWS pre-signed URL with an expiration. Although an AWS pre-signed URL is secure, anyone with the pre-signed URL has access to the PDF.
Option 2: Download the binary directly
In the create PDF API, when setting the export_type to "file", we will return the binary data of the generated PDF, and the response HTTP header Content-Disposition is set to attachment. In this case, we do not store the PDFs on our CDN.
However, there is a payload limit of 6MB for a generated PDF.
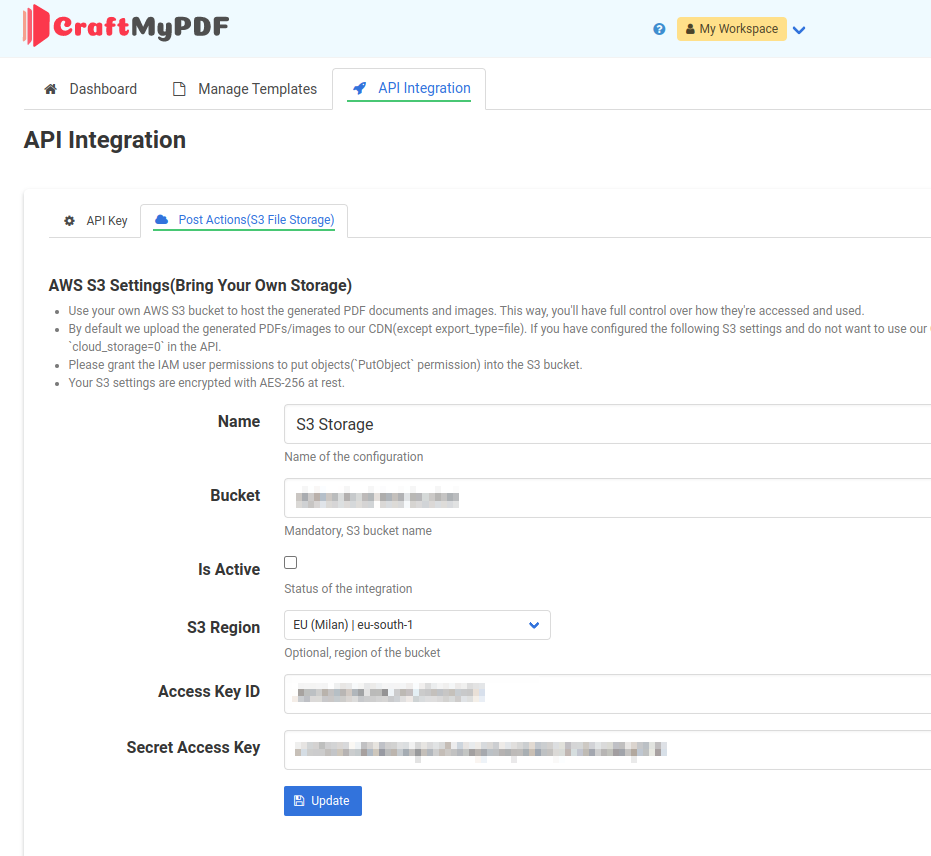
Option 3: Bring Your Own Storage(AWS)
The most secure way is to configure uploading the PDFs/images directly to your AWS S3, and we never store the PDFs. To configure this, click on the API Integration tab. Then, select Post Actions and enter your S3 settings.
Additional information:
- By default we upload the generated PDFs/images to our CDN(except export_type=file). If you have configured the following S3 settings and do not want to use our CDN, please disable the cloud upload by setting the parameter cloud_storage=0 in the API.
- Please grant the IAM user permissions to put objects(PutObject permission) into the S3 bucket. Your S3 settings are encrypted with AES-256 at rest.
*Note: By default, we log incoming requests for up to 14 days. If your requests contain sensitive data and you do not want us to store the data, please consider turning off the request logging.